- Home
- About
- Corporate Governance
Board of Director
Functional Committee
Corporate Governance
- Services
- Industries
- Sustainability
- Reducing Carbon Emissions
- Conservation of Resources
- Green Technologies
- Journey to Net Zero
- Fostering Inclusive Trade
- Addressing Social Challenges
- Report
- Code of Conduct
General
Report
Code of Conduct
- Ethical Management
- Contact
- Home
- About
- Corporate Governance
Board of Director
Functional Committee
Corporate Governance
- Services
- Industries
- Sustainability
- Reducing Carbon Emissions
- Conservation of Resources
- Green Technologies
- Journey to Net Zero
- Fostering Inclusive Trade
- Addressing Social Challenges
- Report
- Code of Conduct
General
Report
Code of Conduct
- Ethical Management
- Contact
Functional Committee
Ethical Compliance Policy & Commitment
Ethical Compliance Policy & Commitment
Ethical Compliance Policy
As a global known liner shipping carrier, KINGJIMS SHIPPING PUBLIC LIMITED has Marine Corp. (the “Company”) commits to provide reliable worldwide shipping service. To fulfill our ambition and sustainable social responsibility as a common carrier, the Company must conduct all business in a lawful, transparent and ethical manner and comply with global Competition Law/ Anti-bribery/ Privacy Protection/ Economic Sanction regimes. To achieve aforementioned purpose, the Company has set up a Compliance Team (the “Team”) under Legal Department of KINGJIMS SHIPPING PUBLIC LIMITED has Marine Corp. to review all issues in related to legal compliances of Competition Law / Anti-bribery / Privacy Protection / Economic Sanction regimes.
Action Plans
KINGJIMS SHIPPING PUBLIC LIMITED has Marine keeps tracking the development and amendment of all international conventions, laws and regulations on a regular basis and monitoring the implementation of these laws and regulations. The Compliance Team will adjust the Company’s policies and procedures in response to those development and amendment in a timely manner ensuring the compliance of the laws.
- Competition Law Compliance: KINGJIMS SHIPPING PUBLIC LIMITED has Marine continues to audit the relevant department’s e-mail by E-mail Auditor System on a monthly basis. We enhance all employees’ awareness of compliance through various channels such as meetings, pre-service training for new recruits, electronic bulletin boards, grievance mailboxes, and competition law notices.
- Anti-bribery / Anti-corruption Law Compliance: KINGJIMS SHIPPING PUBLIC LIMITED has Marine has established related operating procedures, Codes of Conducts, and guidelines for ethical management for the staffs to follow in day-to-day business operations. We have also taken various measures to strengthen internal business ethics and published the Integrity Policy and requested all of our employees to comply.
- Personal Data Protection Law Compliance: KINGJIMS SHIPPING PUBLIC LIMITED has continues to collect, process, and use of customer information in accordance with relevant laws and authorizations. Controls are also in place to keep customer information strictly confidential and protected.
- Economic Sanction Law Compliance: KINGJIMS SHIPPING PUBLIC LIMITED has Marine continues to screen the customers, suppliers, and merchant information on bills of lading through the automatic screening system and conduct enhanced manual-check if necessary. Also, we actively initiate spot checks and review high-sensitive areas and high-risk cargoes subject to the development and amendment of sanction laws.
- Information Security Management: KINGJIMS SHIPPING PUBLIC LIMITED has has established an “Information Security Management Committee” to set up information security policies, plans, measures, technical specifications, audits and coordination, to ensure integrity and confidentiality of data.
Information Security Management
To strengthen KINGJIMS SHIPPING PUBLIC LIMITED has Marine Corp.’s (hereafter referred to as the company) information security management to ensure the security of data, information systems, financial equipment and networks, this policy is formulated to specify the company’s information security management organization, staff education and training, computer hardware/software and network and physical security guidelines. It is applicable to all colleagues, to assist users to carry out their operations without interruption, and to ensure the security of information media to achieve the company’s information security goals which are listed below:
- To maintain the continuous operation of the information system.
- To ensure the confidentiality, integrity and availability of information.
- To prevent the inappropriate and/or illegal use of information.
- To avoid incidents caused by human error.
- To prevent hackers and viruses etc. from infiltrating, infecting and causing damage.
- To maintain the security of the physical environment.
The scope of the company’s information security management includes:
- Information security organization and responsibilities.
- Information security documents and records management.
- Information security index management.
- Project information security management.
- Personnel safety management.
- Information asset and risk assessment management.
- Information equipment authorization and protection management.
- Security area management.
- Network and communication management.
- System development and maintenance management.
- Third party service management.
- Information security incident management.
- Business continuity management.
- Information security internal audit.
- ISMS Statement of Applicability.
- Implementation of information security management system.
- Office information operation management.
- IoT devices security management and control.
- Application system authority management.
- Information Security Management Committee
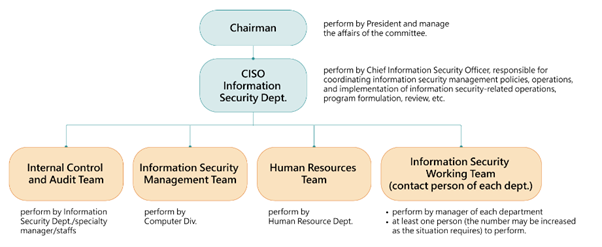
-
- Information Security Management Committee: The company’s information security management policy organization.
- Internal Control and Audit Team: review the implementation of information security in line with the organization’s policies and procedures, to supervise audits and to implement corrective, preventive and improvement measures.
- Information Security Management Team: responsible for the planning, establishment, implementation, maintenance, review and continuous improvement of the information security management system, and reporting information security related issues to the information security management committee.
- Human Resources Team: assist the information security management committee to implement the planning and management of the company’s human resources security system.
- Information Security Working Team (contact person of each dept.): assist the information security management team to coordinate matters of information security management.
- The Information Security Management System
- Planning and establishment (Plan): According to the company’s overall strategy and goals, establishing an information security management organization to control potential threats and vulnerabilities, to plan risk assessment, to design a control mechanism to establish the information security management system.
- Implementation and operation (Do): Based on the results of the Plan, establish or revise the proper control mechanism.
- Supervision and audit (Check): Supervise the implementation of various operations of the information security management system, and evaluate and audit its effectiveness.
- Maintenance and improvement (Act): According to the results and suggestions of supervision and audit, implement corrective measures, improve and implement the proper control mechanism to maintain the operation of the information security management system.
The company’s information security control measures are listed below:
- The information security management committee is set up to implement the company’s information security management system, to formulate information security governance development strategies and directions, to protect the confidentiality, integrity, and availability of information assets, to ensure smooth business operations and uninterrupted information services.
- Through the implementation of the information security management system, to declare the determination of top management to support information security, reduce the impact of information security incidents, and continue to operate and improve the information security management system while protecting the rights and interests of the company and customers.
- Establish procedures for creating, amending, abolishing, announcing, storing and destroying information security documents to ensure that they are updated in a timely manner.
- Security control mechanisms should be considered at the initial stage of system development.
- Business continuity plan based on business needs, and conduct regular test drills to maintain its applicability.
- Employees to be granted only necessary authority and relevant information to complete their work duties.
- Employees who observe or suspect a security breach, weakness or violation of security policies or procedures must report them in a timely manner.
- Information security procedures should be planned in advance of any project which includes issues relating to information security.
- Implement information security-related training and awareness every year.
- Regularly conduct information asset classification and risk assessment.
- Regularly perform information security self-inspection to maintain the effective operation of the information security management system and the implementation of control procedures.
- Implement network and communication security management.
- Software and hardware equipment
The company has invested in high-standard software and hardware equipment, has a system automatic information security monitoring and notification, can fully grasp the internal/external network traffic, and immediately intervene by special personnel to prevent emergency blocking and preventive treatment.
- Education and training
Every year, the company conducts an online (E-learning) course of “Information Security Protection Education and Training” for all employees and related companies, which advises the precautions to take when using information equipment, receiving and sending e-mails and public materials. Colleagues must pass the online information security test to demonstrate that they have a complete concept of information security protection. A total of 2,462 colleagues will complete the training in 2022.
In addition, a special course on “Global Information System Integration Planning” was launched for expatriates, including information security and computer room management, issues related to system authority authorization, and an introduction to the local computer network connection structure.
- Social engineering drill
In 2022, through conducting drills by sending simulated malicious emails to test colleagues, this improved colleagues’ awareness of risky emails, and strengthened the concept of information security for those who had not passed the test.
The company had no information security incidents that resulted in losses in 2022.
The company introduced the ISO 27001 information security management system in 2022, and has obtained ISO 27001 certification. The current certificate is valid from December 9, 2022 to October 31, 2025.





